At a restaurant, you overhear people discussing an interesting case they treated while working in a dental office that day. Which type of regulated data policies are most likely to have been violated?
PII
PHI
PCI
GDPR
PHI
You might also like to view...
Introduce specialization/generalization concepts into the ER model shown in Figure 13.11 and described in Exercise 12.13 to show the following:
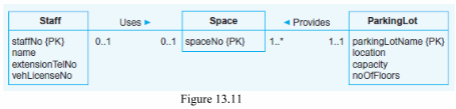
(a) The majority of parking spaces are under cover and each can be allocated for use by a
member of staff for a monthly rate.
(b) Parking spaces that are not under cover are free to use and each can be allocated for use
by a member of staff.
(c) Up to twenty covered parking spaces are available for use by visitors to the company.
However, only members of staff are able to book out a space for the day of the visit. There is no charge for this type of booking, but the member of staff must provide the visitor’s vehicle
license number.
What is displayed after line 6 is run?
```
1 queue
Examples of pull technology include online social networks and photo- and video-sharing sites.
Answer the following statement true (T) or false (F)
Which of the following occurs when two access points share the same SSID broadcast where one access point is used to capture data?
A. Rogue access point B. Bluesnarfing C. Evil twin D. Packet sniffing