In order to generate a public and private key for use with SSH, what command line utility should you use?
a. ssh-keygen
b. key-generate
c. ssh-newkey
d. gpg --ssh
ANSWER: a
You might also like to view...
Configure switch 1 (sw1), router R1, PC1, PC2, and S1 using the IP addresses provided in Table 1. The IP addresses used in this exercise will all be configured as part of a 192.168.5.0 network.
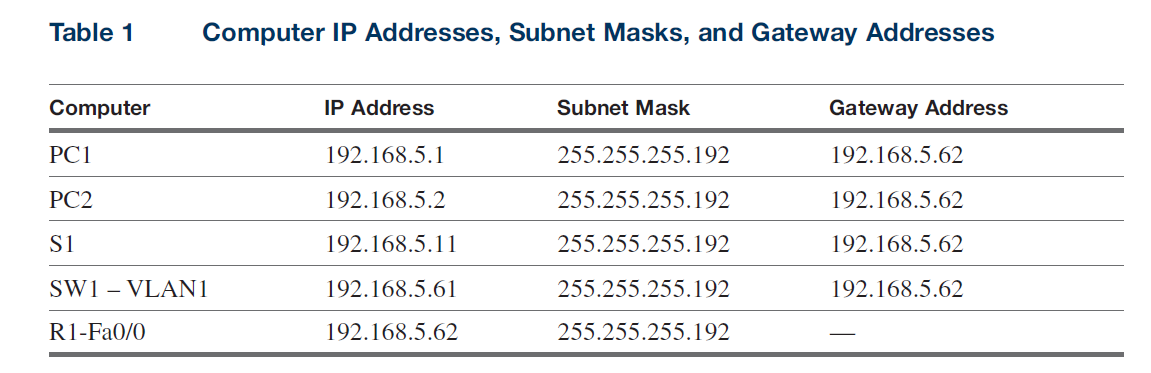
1. Your first task is to configure the switch SW1, the Router R1, the computers PC1 and PC2, and the switch S1 for the network provided in Figure 1. Use the IP addresses provided in Table 1.
2. After you have completed configuring the interfaces, verify that you have connectivity with all interfaces. List the commands used to verify network connectivity. Correct problems as needed.
3. Check whether port security has been enabled on the switch port connected to server S1 by using the show port-security interface Gi0/1 command. Record the status of the port security configuration on the interface based on the first line of output.
4. Configure port security using three commands: one command to make the port a statically configured access port, one command to enable port security, and one command to define the allowed MAC address, namely, S1’s MAC address of 0200.AAAA.AAAA. Record the three commands you used on the lines below.
5. Move back to enable mode and repeat the comman
To edit a slide master in PowerPoint, click Slide Master on the ________ tab
A) REVIEW B) VIEW C) SLIDE SHOW D) DESIGN
A developer already created a database for the small business you work for. Your supervisor likes the way that the database performs, but needs some changes made to the reports that are part of the database. The "Finance Report" needs a new title. How do you change the title of the "Finance Report" to "Accounts Payable"?
What will be an ideal response?
Given the following input records, how many lines would be output if a control break program was used to output a group-indicated report, containing intermediate lines but not final totals or heading lines?
John 20.00 John 30.00 Mary 10.00 Sue 6.00 Sue 8.00 Sue 13.00 a) 3 b) 4 c) 9 d) 10