Labels on the vertical axis can be rotated to display parallel to the vertical axis
Indicate whether the statement is true or false
TRUE
Computer Science & Information Technology
You might also like to view...
Testing a function or program using test values that are at or near the values that change the outcome of the program is known as using
a. parameters b. functional decomposition c. boundary values d. a black-box
Computer Science & Information Technology
Considering the graph G shown in Figure 9.1
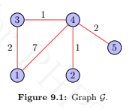

Computer Science & Information Technology
____________________ access calls for using a unique physical characteristic of a person to permit access to a controlled IT resource.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The final step in the process of initially securing the base operating system is ________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology