Which of the following is the first step in the digital signature process where Mike sends a message to Sophie?
A. a message digest of Mike's message is calculated using a hashing algorithm
B. Sophie compares the message digest she calculated to Mikes's message
C. Sophie encrypts Mike's message with Mike's public key
D. the message digest is encrypted by Mike's private key
Answer: A
You might also like to view...
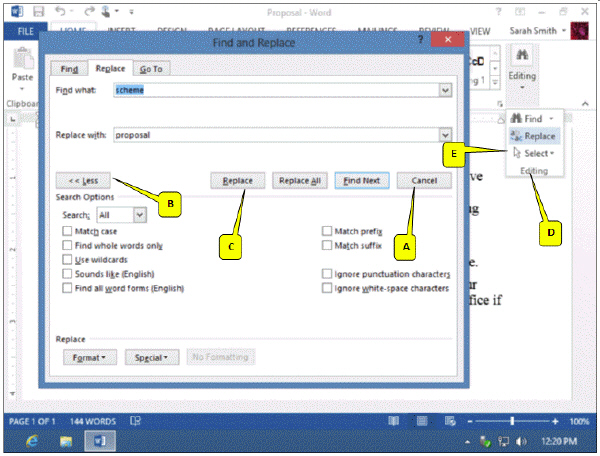 Refering to the accompanying figure, which of the following search options should be selected if you are looking for all search string matches in any part of the word?
Refering to the accompanying figure, which of the following search options should be selected if you are looking for all search string matches in any part of the word?
A. Match case B. Find whole words only C. Use wildcards D. none of the above
You can remove a slide from a presentation by selecting a slide thumbnail and then tapping the ____________________ key.
Fill in the blank(s) with the appropriate word(s).
A separate ________ should be completed for each computer that is analyzed, which should note Case Number, Date, Location, Make, Model, and Serial Number
Fill in the blank(s) with the appropriate word(s).
In the United States, freedom of expression
a. is a positive right. b. is not an absolute right. c. is limited to political speech. d. has been abolished by decisions of the U.S. Supreme Court. e. is guaranteed by the Fourth Amendment to the U.S. Constitution.