Derek’s supervisor is concerned that the company’s security system does not comply with the new standards the company has decided to employ. She has asked Derek to determine how members of the company are authenticated on the network.
What does the computer or server use to verify the access to a specific resource on the network?
A. Access control list
B. Directory permissions
C. Login script
D. Digital Certificate
Answer: A
You might also like to view...
________ allows an application to track data across multiple Web pages.
a) A Response object b) Client state c) An instance variable d) Session state e) None of the above.
Using RMI, write an application for a prototype opinion poll system. Assume that only one issue is being polled. Respondents may choose yes, no , or don't care. Write a server application to accept the votes, keep the tally (in memory), and provide the current counts to those who are interested.
What will be an ideal response?
In the accompanying figure of a Microsoft Word 2016 document, which of the following boxes is pointing to the paragraph mark??
?
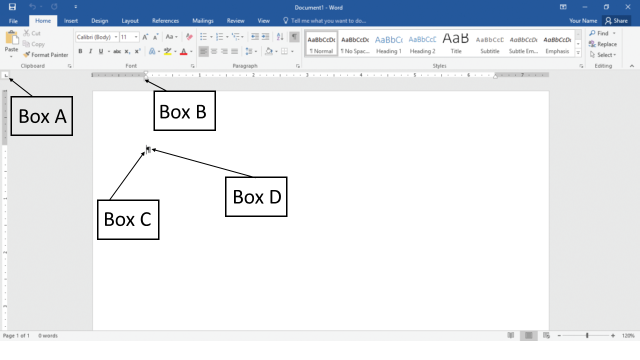
A. ?Box A B. ?Box B C. ?Box C D. ?Box D
The network administrator has configured the enterprise firewall to permit port 21 to allow FTP transfers to occur from outside the enterprise. Users can connect to the FTP server that is located on the enterprise network. However, file transfers fails. Why could this be?
UDP port 21 TCP port 20 TCP port 21 UDP port 20