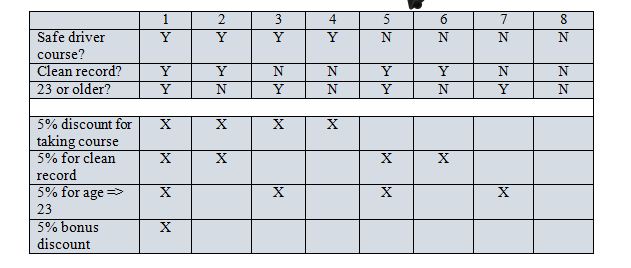
Create a decision table that describes the discount rules.
What will be an ideal response?
Computer Science & Information Technology
You might also like to view...
Denial of service attacks target which of the following?
A) Availability B) Integrity C) Security D) Confidentiality
Computer Science & Information Technology
Match each of the following parts of this URL to its definition: http:// http://www.si.edu/Exhibitions
I. si.edu II. Exhibitions III. http:// IV. .edu A. top-level domain B. folder or subdirectory C. domain D. protocol
Computer Science & Information Technology
The What-If Analysis tool is on the ________ tab
A) Insert B) Home C) View D) Data
Computer Science & Information Technology
?Describe the process of setting the width and color of a border.
What will be an ideal response?
Computer Science & Information Technology