What is the value of ANSWER after the instructions corresponding to the following pseudocode are executed?
```
COUNT = 5
SUM = 100
DOUNTIL COUNT < 5
SUM = SUM + 5
COUNT = COUNT - 1
ENDDO
ANSWER = SUM
```
a) 5
b) 100
c) 105
d) 125
c) 105
You might also like to view...
Which of the following is the first packet sent in the TCP three-way handshake?
A. RST B. SYN C. ACK D. PSH
What happens to Windows Command Processor and Console Window Host when the command prompt window is closed?
What will be an ideal response?
Working in the Processes Tab
a. Open a command prompt and a web browser.
Microsoft Edge is used in this lab; however, any web browser will work. Just substitute your browser name whenever you see Microsoft Edge.
b. Right-click the Task bar to open Task Manager. Another way to open the Task Manager is to press Ctrl-Alt-Delete to access the Windows Security screen and select Task Manager.
c. Click More details to see all the processes that are listed in the Processes tab.
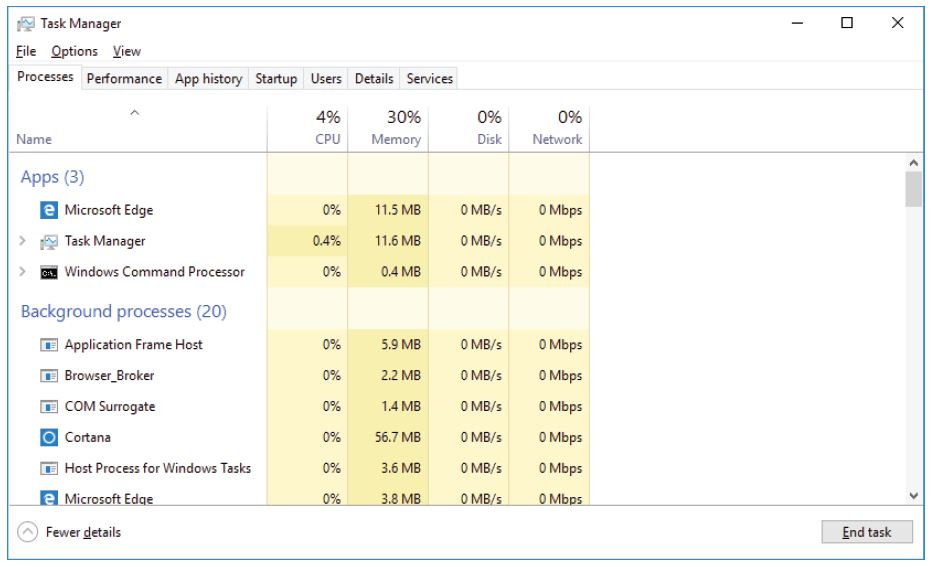
d. Expand the Windows Command Processor heading.
e. There are three categories of processes listed in the Processes tab: Apps, Background processes, and Windows processes.
? The Apps are the applications that you have opened, such as Microsoft Edge, Task Manager, and Windows Command Processor, as shown in the figure above. Other applications that are opened by the users, such as web browsers and email clients, will also be listed here.
? The Background processes are execut
____ is a process that scrambles the data so that it cannot be read if intercepted by unauthorized users.
A. Encryption B. Decryption C. Deciphering D. Decoding
?Matching: separation of duties - sensitivity levels - storage channel - task-based controls - timing channel - TCB - blueprint - DAC - content-dependent access controls - rule-based access controls
A. A framework or security model customized to an organization, including implementation details. B. Controls implemented at the discretion or option of the data user. C. Controls access to a specific set of information based on its content. D. Access is granted based on a set of rules specified by the central authority. E. Requires that significant tasks be split up in such a way that more than one individual is responsible for their completion. F. Ratings of the security level for a specified collection of information (or user) within a mandatory access control scheme. G. One of the TCSEC's covert channels, which communicate by modifying a stored object. H. A form of non discretionary control where access is determined based on the tasks assigned to a specified user. I. A TCSEC-defined covert channel, which transmits information by managing the relative timing of events. J. Within TCSEC, the combination of all hardware, firmware, and software responsible for enforcing the security policy.