Signature-based IDPS technology is widely used because many attacks have clear and distinct signatures.
Answer the following statement true (T) or false (F)
True
You might also like to view...
Consider six transactions T 1 , T 2 , T 3 , T 4 , and T 5 with:
T 1 initiated at site S 1 and spawning an agent at site S 2 ,
T 2 initiated at site S 3 and spawning an agent at site S 1 ,
T 3 initiated at site S 1 and spawning an agent at site S 3 ,
T 4 initiated at site S 2 and spawning an agent at site S 3 ,
T 5 initiated at site S 3 .
The locking information for these transactions is shown in following table.
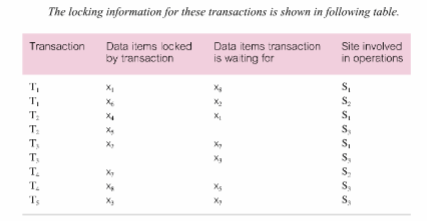
(a) Produce the local wait-for-graphs (WFGs) for each of the sites. What can you conclude from the local WFGs?
(b) Using the above transactions, demonstrate how Obermarck’s method for distributed deadlock detection works. What can you conclude from the global WFG?
An example of a free Web-based e-mail service is ________
Fill in the blank(s) with correct word
________ indexes place marked entries and subentries on separate lines with spacing before each indexed item
A) Indented B) Run-in C) Cross-referenced D) Table
The design that determines how data is displayed or compared in a chart is the chart ________
Fill in the blank(s) with the appropriate word(s).