There are always __________ steps that must be taken when a file is used by a program.
Fill in the blank(s) with the appropriate word(s).
three
You might also like to view...
Which of the following are potential problems when we assign pointer variables:
a. inaccessible heap memory b. dangling pointers c. uninitialized pointers d. NULL pointers
The ‘Transfer’ transactions T and U are defined as:
T: a.withdraw(4); b.deposit(4);
U: c.withdraw(3); b.deposit(3);
Suppose that they are structured as pairs of nested transactions:
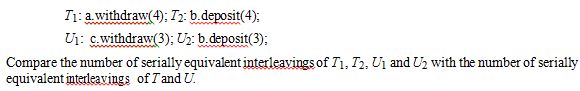
Explain why the use of these nested transactions generally permits a larger number of serially equivalent interleavings than non-nested ones.
When handouts exported from PowerPoint to Word are saved in Word, the extension on the Word file will be ________
Fill in the blank(s) with correct word
What value will Access calculate from the following formula: =1+(2-3)+5/6-6^2?