A security administrator wishes to implement a method of generating encryption keys from user passwords to enhance account security. Which of the following would accomplish this task?
A. NTLMv2
B. Blowfish
C. Diffie-Hellman
D. PBKDF2
Answer: C. Diffie-Hellman
Computer Science & Information Technology
You might also like to view...
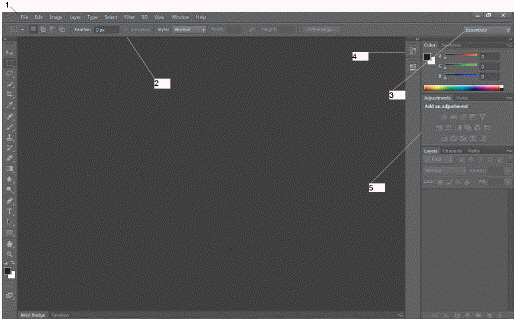 In the accompanying figure, which number represents the workspace options?
In the accompanying figure, which number represents the workspace options?
A. 1 B. 2 C. 3 D. 4
Computer Science & Information Technology
A small box that displays the name of a screen element or information about it is called a ________
A) ScreenHint B) ScreenShot C) ScreenClue D) ScreenTip
Computer Science & Information Technology
The ____ lists the contents of a folder.
A. message list B. Navigation Pane C. Reading Pane D. message pane
Computer Science & Information Technology
What technology provides fault tolerance and improved performance in a connection between a client and a server providing an SMB share?
What will be an ideal response?
Computer Science & Information Technology