When using an Excel table, a table can do all of the following EXCEPT ________
A) automatically adjust table formatting and formula references
B) provide both flexibility and scalability
C) automatically sort data in table columns
D) help provide context to the user by organizing data in a meaningful way
Answer: C
You might also like to view...
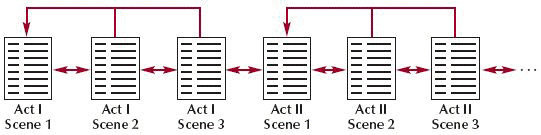 The structure shown in the accompanying figure is an augmented linear structure.
The structure shown in the accompanying figure is an augmented linear structure.
Answer the following statement true (T) or false (F)
Which of the following is NOT a problem in the investigation of cybercrime?
a. perceived insignificance of cybercrime b. prosecutorial reluctance to pursue cyber criminals c. untrained investigators d. a widespread perception of cybercrime as worse than "traditional" crime
Not all __________ access is malicious, but it should still be prevented; for example, a user may poke around a network share and see sensitive information.
Fill in the blank(s) with the appropriate word(s).
Which of the following protocols uses AES and the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP) for wireless data encryption?
A. WEP B. WPA3 C. WPA2 D. WPA