Merge fields are codes that are replaced with the field values when the mail merge is processed.
Answer the following statement true (T) or false (F)
True
You might also like to view...
This attack uses a spoofing technique to carry out the attack. The attacker spoofs the victim’s IP address and sends requests many different servers or devices that respond to that type of re-quest. The devices all then reply back to the victim’s IP address, which is unable to process the overwhelming amount of traffic.
What will be an ideal response?
What is the difference between batch processing and using the Image Processor?
What will be an ideal response?
Google+ circles define ________ relationships; thus, when you add someone to one of your circles, you are not automatically added to that person's circles
A) joined B) multiple-way C) two-way D) one-way
Translate the above diagram into the relational model by supplying the appropriate CREATE TABLE statements. Note that ISBN is a 10-digit string (which can have leading zeros), sex can have only two values, 'M' or 'F', and a phone number is a 10 digit number that never starts with a zero. Specify these as domains.
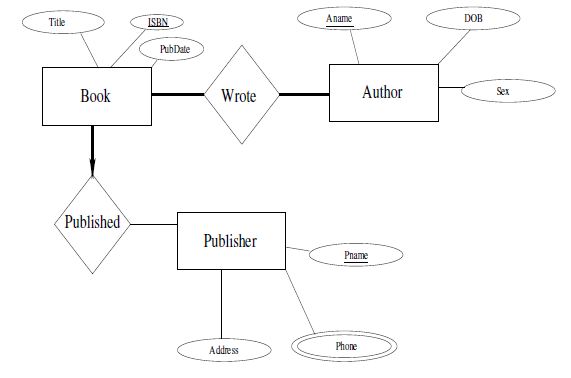
Specify all the key and foreign key constraints. Try to preserve as many participation
constraints as possible. List all the participation constraints that are present in the E-R
diagram, but not in its translation to SQL.