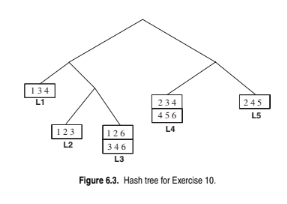
Construct a hash tree for the above candidate 3-itemsets. Assume the tree uses a hash function where all odd-numbered items are hashed to the left child of a node, while the even-numbered items are hashed to the right child. A candidate k-itemset is inserted into the tree by hashing on each successive item in the candidate and then following the appropriate branch of the tree according to the hash value. Once a leaf node is reached, the candidate is inserted based on one of the following conditions: Condition 1: If the depth of the leaf node is equal to k (the root is assumed to be at depth 0), then the candidate is inserted regardless of the number of itemsets already stored at the node. Condition 2: If the depth of the leaf node is less than k, then the candidate can be inserted as long
Consider the following set of candidate 3-itemsets:
{1, 2, 3}, {1, 2, 6}, {1, 3, 4}, {2, 3, 4}, {2, 4, 5}, {3, 4, 6}, {4, 5, 6}
Computer Science & Information Technology
You might also like to view...
A button component should have a registered _____________ associated with it.
a. pixel b. JFrame c. listener d. none of the above
Computer Science & Information Technology
A(n) ________ is a high-end desktop computer or one that is connected to a network in a business setting
A) workstation B) two-in-one C) netbook D) all-in-one
Computer Science & Information Technology
The Application layer receives packets from the ____ layer and opens them to convert the message back to its original form.
A. Data Link B. Transport C. Physical D. Internet
Computer Science & Information Technology
A(n) ________ is a collection of multiple objects on a presentation slide treated as one unit
A) index B) table of figures C) macro D) group
Computer Science & Information Technology