The system and application security competency has the required functional perspective of ____.
A. manage, design
B. manage
C. manage, design, evaluate
D. manage, evaluate
Answer: D
You might also like to view...
Refer to the following function for Question:
``` int six (int n) { int ans; if (n <= 1) ans = 1; else if (n % 2 == 0) ans = n * six (n - 2); else ans = six (n - 1); return ans; } ``` What value is returned by function six for the call six (9); ? a. 8 b. 48 c. 945 d. 384 e. 383
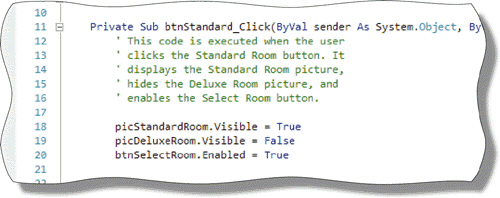 As shown in the accompanying figure, ____________________ are non-executable statements inside the program explaining the programmatic steps.
As shown in the accompanying figure, ____________________ are non-executable statements inside the program explaining the programmatic steps.
Fill in the blank(s) with the appropriate word(s).
Someone who finds a flaw in a system and reports that flaw to the vendor of the system is a __________
a. White hat hacker b. Black hat hacker c. Gray hat hacker d. Red hat hacker
Which statement is not correct? The structured design approach
A. is a top-down approach B. is documented by data flow diagrams and structure diagrams C. assembles reusable modules rather than creating systems from scratch D. starts with an abstract description of the system and redefines it to produce a more detailed description of the system