Match each item with a statement below.
A. Uses two keys: one to encrypt data and one to decrypt data
B. Encryption algorithm used for the Data Encryption Standard
C. Uses a single key to encrypt and decrypt data
D. A digital document that verifies the two parties exchanging data over the Internet are really who they claim to be
E. Used for verification, takes a variable-length input and converts it to a fixed-length output string
F. Used to find the same hash value for two different inputs and reveal any mathematical weaknesses in a hashing algorithm
G. Operate on plaintext one bit at a time
H. A structure consisting of programs, protocols, and security policies for encrypting data and uses public key cryptography to protect data transmitted over the Internet
I. A sequence of random bits generated from a range of allowable values
J. The use of random data alongside plaintext as an input to a hashing function so that the output is unique
A. asymmetric algorithm
B. DEA
C. symmetric algorithm
D. certificate
E. hashing algorithm
F. birthday attacks
G. stream cipher
H. PKI
I. key
J. salt
You might also like to view...
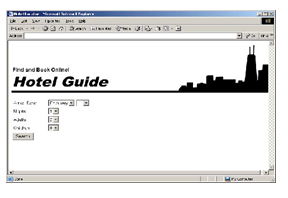
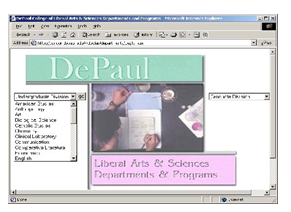
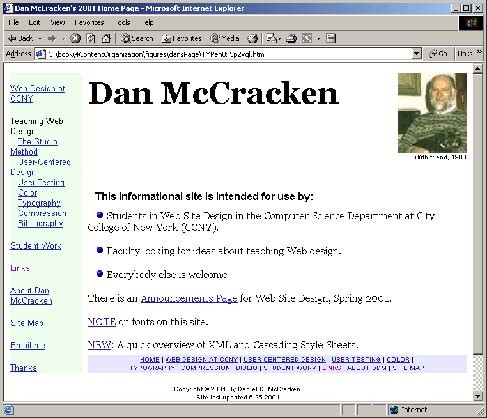
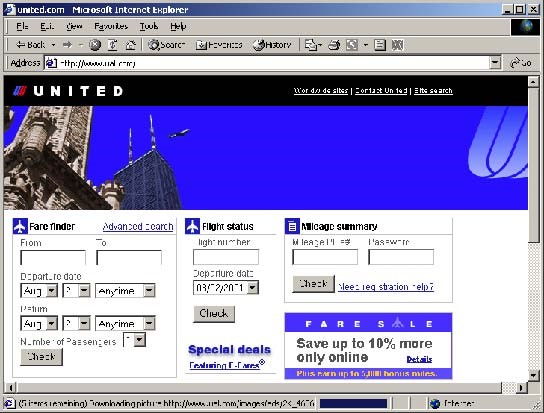
Name the organizational structure being used on each of the following Web pages.
Figure;

What is the difference between guided and unguided transmission?
What will be an ideal response?
Match the following file types to their description
I. Sockets A. Unbuffered files used to exchange data II. Character devices B. Virtual connections between two processes III. Named pipes C. Provide a FIFO mechanism IV. Block devices D. Buffered files used to exchange data
In a(n) _____ backup, copies of the files that have changed since the last full system backup are recorded.
A. selective B. differential C. status D. incremental