Business users in particular have responsibilities with respect to the use of networking resources.
Answer the following statement true (T) or false (F)
True
Computer Science & Information Technology
You might also like to view...
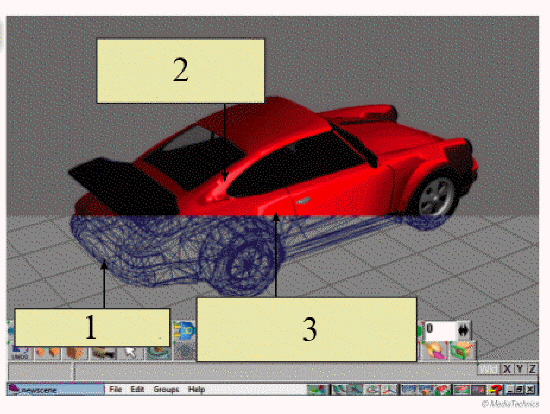 In the figure above, the rendering process referred to by item 2 ____.
In the figure above, the rendering process referred to by item 2 ____.
A. creates a wireframe B. traces the rays of light from the light source to the object C. creates textured surfaces D. colors the object in
Computer Science & Information Technology
Phishing is a type of span that tries to trick users into giving up information such as passwords
Indicate whether the statement is true or false
Computer Science & Information Technology
In the right pane in the Printers window, the ____ heading lists the names of printers managed through the Printers window.
A. name B. description C. location D. path
Computer Science & Information Technology
The function ____________________ is the lines of code that make up a function
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology