Targeted attacks against financial networks, unauthorized access to information, and the theft of personal information are sometimes known as ____________________.
Fill in the blank(s) with the appropriate word(s).
cybercrime
Computer Science & Information Technology
You might also like to view...
When creating a multitable query, in the top section of the query design, you use ________ lines to connect common fields in related tables
A) connection B) relationship C) common field D) join
Computer Science & Information Technology
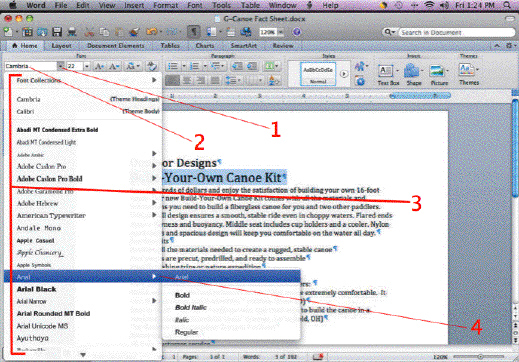 In the accompanying figure, Item 4 points to the ____.
In the accompanying figure, Item 4 points to the ____.
A. disclosure triangle B. Font Size pop-up menu arrow C. Font pop-up menu arrow D. Font group pop-up menu arrow
Computer Science & Information Technology
If you want to see which employee had the highest sale, you could use the ________ function
A) MAX B) SUM C) COUNT D) MIN
Computer Science & Information Technology
Which of the following is NOT a comparison operator symbol?
A) ? B) < C) >= D) =
Computer Science & Information Technology