SYN flood attacks and UDP flood attacks are an example of which of the following?
a. Viruses
b. DoS attacks
c. IP spoofing attacks
d. Trojans
ANS: B
Computer Science & Information Technology
You might also like to view...
The heart of a database is forms because they contain the actual data
Indicate whether the statement is true or false
Computer Science & Information Technology
The time a task can be delayed from its scheduled start date without delaying the project is called ________
A) scope B) critical path C) slack D) task dependency
Computer Science & Information Technology
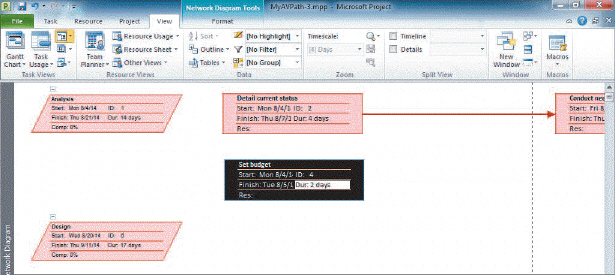 The boxes with minus signs at the upper-left corner of the red boxes indicate that the item is________.
The boxes with minus signs at the upper-left corner of the red boxes indicate that the item is________.
A. indexed B. summarized C. expanded D. collapsed
Computer Science & Information Technology
How is data stored in a NoSQL database?
What will be an ideal response?
Computer Science & Information Technology