Why are new developers somewhat of a risk to the security of the software?
A. they don't have the background knowledge that the developers who wrote the software do
B. they may not know the CCB process
C. they might know how to report incidents
D. they may not know the Application Guide
Answer: A
You might also like to view...
Answer the following statements true (T) or false (F)
1. The du command displays how many times a disk is used. 2. The df command shows the disk failure messages. 3. You can create your own spelling dictionary file. 4. The at command is used to run programs at a specified time. 5. The passwd file contains most of the information system needs to know about a user.
Describe these logical processor options: Virtual machine limit and Relative weight.
What will be an ideal response?
What is SmartArt, and how do you enter text in a SmartArt graphic?
What will be an ideal response?
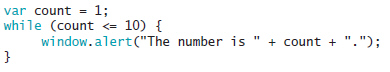 Which of the following statements most accurately describes the code in the accompanying figure?
Which of the following statements most accurately describes the code in the accompanying figure?
A. It will not print "1". B. It will never exit. C. The value of the counter is changed in the loop. D. A do...while loop should be used instead.