Ayman’s Office Supplies Company recently had a new information system installed to help its managers with inventory. In speaking with the managers, you notice that they seemed disgruntled with the system output, which is a series of displays that show current inventory, customer and supplier addresses, and so on. All screens need to be accessed through several special commands and the use of a password. The managers had several opinions about the system but had no systematic way to evaluate it.
a. Devise a checklist or form that helps Ayman’s managers evaluate the utilities of an information system.
b. Suggest a second way to evaluate the information system.
a. A suitable checklist to use in this situation would be the use of information system utility approach.
1) Form Utility: Is the output format acceptable? Is it suitable? Is it easy to understand?
2) Time Utility: Is the information up to date? Is feedback fast enough?
3) Place Utility: Are screen outputs accessible to the managers? Is the computer located at a convenient place?
4) Possession Utility: Are managers able to receive information? Are the passwords keeping the authorized personnel only to access the information? Do managers have problems with accessing the information using passwords?
5) Implementation Utility: Was implementation easy? Did all users get involved with design of output? Was the trial period successful?
6) Actualization Utility: Would the system be considered as beneficial? Will satisfactory and long-lasting results occur?
7) Goal Utility: Did the system fulfill user requirements? Are all the objectives of the system met?
b. Another approach that can be used is the user involvement approach. It provides a checklist of dysfunctional behavior by various organizational members and provides an insight for future projects
You might also like to view...
Code a method that finds the last occurrence of an object in an array. The method should return the index of the object if found and –1 if not found.
What will be an ideal response?
The accompanying figure shows an example of how to cite an online article using different style formats. Box 2 constitutes the _____ style format.
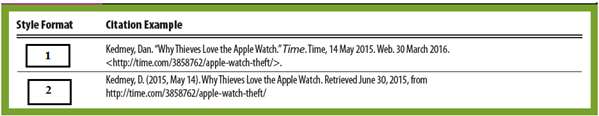
A. ?MLA B. ?APA C. ?URL D. ?http
The "stored programming" concept developed by John von Neumann states that any program can be written by using only sequence, selection, and repetition structures.
Answer the following statement true (T) or false (F)
Identify the letter of the choice that best matches the phrase or definition.
A. In numerical order from lowest to highest number B. In numerical order from highest to lowest number C. Can be done to create a heading to span across two or more columns D. Can be used to create two tables from one E. Enables you to remove cell boundaries from a table