The term ____ refers to those individuals who break into our networks without authorization with the hope of destroying and/or stealing information.
A. cracker
B. consultant
C. hacker
D. defender
Answer: A
You might also like to view...
(Computer Monitor Invoice GUI) In this exercise, you apply the GUI design guide- lines you have learned to a graphical user interface for an invoicing application (Fig. 3.24). You will specify the bounds of the JTextFields in the rows of the GUI that begin with the 15", 17" and 19" JLabels.
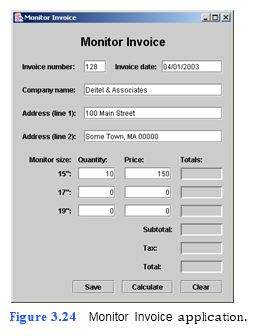
a) Copying the template to your working directory. Copy the C:Examples Tutorial03ExercisesMonitorInvoice directory to your C:SimplyJava direc- tory.
b) Opening the Command Prompt window and changing directories. Open the Com- mand Prompt by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:SimplyJavaMonitorInvoice, then pressing Enter.
c) Compiling the template application. Compile your application by typing javac
MonitorInvoice.java, then pressing Enter.
d) Running the template application. Run the application by typing java MonitorIn- voice. The GUI of the Monitor Invoice template application should appear as shown in Fig. 3.25.
e) Closing the application. Close your running application by clicking its close button. f) Opening the template file. Open the MonitorInvoice.java file in your text editor.
g) Customizing the JTextFields below the Quantity: JLabel. Using Fig. 3.24 and the template code
Which of the prototypes below would not be a valid overloaded function?
Given the overloaded function prototype: void CalcShape(int w); A. int CalcShape(int w, float p); B. void CalcShape(int w, int y); C. float CalcShape(int w); D. void CalcShape(char b);
Database designers can disable all but the form view to protect the form's design and layout
Indicate whether the statement is true or false
Critical thinking typically includes passively thinking about the issue, asking questions, analyzing and evaluating evidence and symptoms, and seeking different perspectives. These activities help you identify and evaluate different options when faced with a problem
Indicate whether the statement is true or false