Dirk Davis purchases a piece of industrial wasteland. He knows that there is contamination in the soil, but he also knows that it is buried very deep and believes that it won't become known for at least 20 years
He incorporates Florida Condos Ltd, builds a condominium tower, and sells all the units – without, of course, disclosing the contamination. He then has the corporation, of which he is sole shareholder and director, distribute all the profits to him as dividend. The contamination "surfaces" within 12 months and the condo owners want to sue. Florida Condos has no assets, however, so they want to sue Dirk personally. Which of the following is FALSE?
A) It is generally very difficult to persuade a court to pierce the corporate veil.
B) It is not enough that it be just and equitable to pierce the corporate veil.
C) Since Dirk knew of the contamination, his conduct was tantamount to fraud and justifies piecing the corporate veil.
D) Dirk will not be liable personally because it was corporation that sold the condos not him personally
E) The court could hold Dirk personally liable for financial losses as well as punitive damages
D
You might also like to view...
On January 1, 2019, Sapphire Manufacturing Company purchased a machine for $40,000,000. The company expects to use the machine for 24,000 hours over the next six years. The estimated residual value of the machine at the end of the sixth year is $40,000. The schedule of usage of the machine is below.
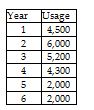
Prepare the depreciation schedule using the units-of-production method of depreciation.
The ____, short for World Wide Web, is an Internet service that provides convenient access to information through hyperlinks.
A. Web B. Net C. Spider D. Wide "W"
Data warehouse front-end applications are often referred to as business intelligence (BI) applications
Indicate whether the statement is true or false
One of the newest trends in ERP is the movement of ERP to cloud systems. The benefits of using cloud systems include less investment in hardware, less software maintenance and the outsourcing of information systems infrastructure. However, one needs to look closely at the security capabilities of your cloud provider, especially when incidences of hacking are more prevalent – managers need to
worry about information security. According to the United States Computer Emergency Readiness Team (US-CERT), several organizations using ERP systems are vulnerable to cyberattack. First, ERP specialists are often database administrators with very little experience in cybersecurity. Second, ERP systems are very complex, with as many as tens of thousands of settings that make cybersecurity difficult. In addition, companies often lack the resources to monitor their ERP systems properly. From a behavioral point of view, firms should never let associates access ERP systems from personally owned computers, tablets, or smartphones, and employees should not be given the use of company computers when they leave a company. Putting off security measures or upgrades because they could potentially disrupt your business operations is never a good idea. The failure to properly secure your data may ultimately put your business's entire future at risk. A) 6 months to 1 year. B) up to 3 months. C) weekly. D) daily.