The accompanying figure shows the working of a _____.
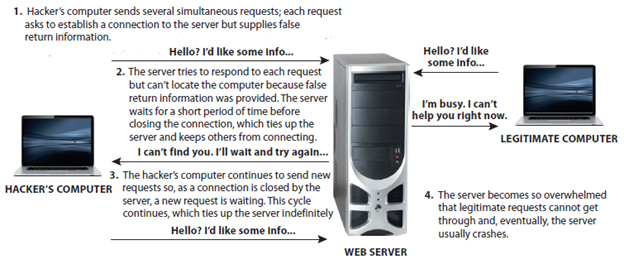
A. ?brute force attack
B. ?denial of service attack
C. ?quick attack
D. ?phishing attack
Answer: B
Computer Science & Information Technology
You might also like to view...
A 2010 survey from Microsoft Research states that ________ percent of companies have rejected applicants based on information found online
Fill in the blank(s) with correct word
Computer Science & Information Technology
You can change the alignment, or position of text within a document's margins, using the alignment buttons in the ____ group on the Home tab of the ribbon.
A. Styles B. Text Layout C. Margins D. Paragraph
Computer Science & Information Technology
For an XHTML document to be well formed, the element must include both the src and ____ attributes.
A. size B. width C. text D. alt
Computer Science & Information Technology
Which version of Simple Network Management Protocol (SNMP) is considered the most secure?
a. SNMPv2 b. SNMPv3 c. SNMPv4 d.SNMPv5
Computer Science & Information Technology