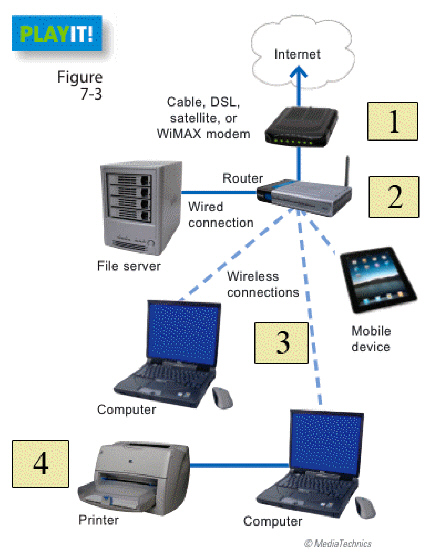
 In the figure above, which item represents the device used to connect to the Internet?
In the figure above, which item represents the device used to connect to the Internet?
A. item 2
B. item 5
C. item 1
D. item 3
Answer: C
Computer Science & Information Technology
You might also like to view...
Most information security functions operate under the dark star of ____________________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
What is short-circuit evaluation of Boolean expressions?
What will be an ideal response?
Computer Science & Information Technology
Modified Multiple Choice After adding a shape to a slide, you can change its default characteristics by adding ____.
A. text B. bullets C. numbers D. styles
Computer Science & Information Technology
A nonmember function must be declared as a(n) _________ of a class to have access to that class’s private data members.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology