Using a private but unsecured Wi-Fi network without authorization is called war driving or ____________________.
Fill in the blank(s) with the appropriate word(s).
Wi-Fi piggybacking
Computer Science & Information Technology
You might also like to view...
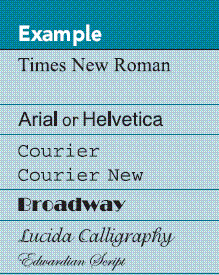 In the accompanying figure, Courier New is an example of a ____ font.
In the accompanying figure, Courier New is an example of a ____ font.
A. fantasy B. serif C. cursive D. monospace
Computer Science & Information Technology
An extranet essentially is a small version of the Internet that exists within an organization.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
What is DumpSec and what can it be used for?
What will be an ideal response?
Computer Science & Information Technology
What is the ten-step business process review methodology?
What will be an ideal response?
Computer Science & Information Technology