Describe an open relay.
What will be an ideal response?
Another major attack involving an SMTP server occurs when an e-mail server administrator does not restrict who can use the SMTP server to send e-mail. This type of configuration is referred to as an open relay. Attackers will scan the Internet looking for open relays that they can use to send spam. This allows the attackers to use the e-mail system to send e-mail anonymously. In the case of worms, malicious software can also use the open relay to propagate itself across the Internet.
You might also like to view...
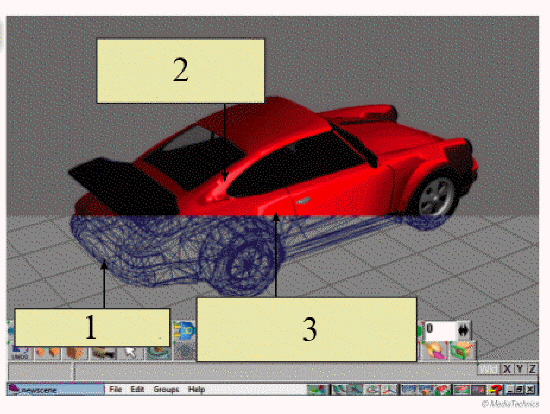 In the figure above, item 3 indicates ray tracing, which is where ____.
In the figure above, item 3 indicates ray tracing, which is where ____.
A. the rendering process begins B. the wireframe begins C. your computer creates highlights where the light rays contact the surface D. the VIN number of the vehicle is located
To match any single numeric character, you would use the ________ wildcard character
Fill in the blank(s) with correct word
Some advanced features work only in specific Web browsers.
Answer the following statement true (T) or false (F)
A clicking noise coming from a system could indicate that a hard drive is failing.
Answer the following statement true (T) or false (F)