The technician has suspicions that a browser has been hijacked. Which of the following should the technician look for in this situation?
A. A new default gateway has been setup.
B. A new Internet shortcut has been added.
C. A new web browser has been installed and is now the default.
D. A proxy server has been enabled.
Answer: D. A proxy server has been enabled.
You might also like to view...
Describe and observe the outcome.
This exercise guides you through experiments with connection-oriented datagram socket using code sample Example4 Compile and run Example4*.java. Start the Acceptor first, then the Requestor. Sample commands to do so are: ``` Java Example4ConnectionAcceptor 12345 Good-day! Java Example4ConnectionRequestor localhost 12345 ```
Match the following Merge Shapes options to their result
I. Fragment II. Union III. Intersect IV. Combine V. Subtract A. Sums two or more shapes B. Breaks shapes in smaller parts C. Sum of two or more shapes less overlapping parts D. Overlapped region between shapes E. Removes whole parts of a shape using the outline of another shape
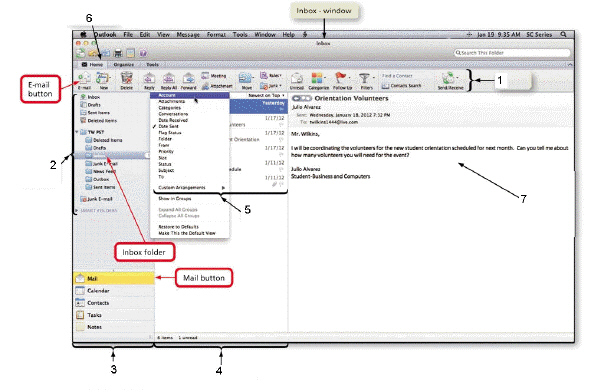 The item numbered 3 in the accompanying figure can be used to browse Outlook folders using all of the following views EXCEPT ____.
The item numbered 3 in the accompanying figure can be used to browse Outlook folders using all of the following views EXCEPT ____.
A. Mail B. Messages C. Contacts D. Tasks
Browsers, search engines, and assistive devices for people with disabilities all use HTML code to help interpret Web pages.
Answer the following statement true (T) or false (F)