Match the following terms with the correct definitions below:?
A. ?The pnrocess of shifting one or more digits in a binary number to the left or right to produce a different value.
B. ?The process of hashing all sectors of a file and then comparing them with sectors on a suspect's disk drive to determine whether there are any remnants of the original file that couldn't be recovered.
C. ?In steganalysis, the original file with no hidden message.
D. ?A technology designed to recover encrypted data if users forget their passphrases or if the user key is corrupted after a system failure.
E. ?An AccessData database containing the hash values of known legitimate and suspicious files. It's used to identify files for evidence or eliminate them from the investigation if they are legitimate files.
F. ?A file containing the hash value for every possible password that can be generated from a computer's keyboard.
G. ?Adding bits to a password before it's hashed so that a rainbow table can't find a matching hash value to decifer the password.
H. ?The result of an investigation expanding beyond its original description because the discovery of unexpected evidence increases the amount of work required.
I. ?A cryptographic technique for embedding information in another file for the purpose of hiding the information from casual observers.
J. ?In steganalysis, the file containing the hidden message.
A. ?bit-shifting
B. block-wise hashing?
C. ?cover-media
D. key-escrow?
E. ?Known File Filter (KFF)
F. rainbow table?
G. ?salting passwords
H. scope creep?
I. ?steganography
J. stego-media
You might also like to view...
Java is considered to be architecture neutral because it
a. can be recompiled to run on many CPUs. b. only needs to be compiled once and can run on many different CPUs. c. can run on many different generations of Windows. d. can run in any browser.
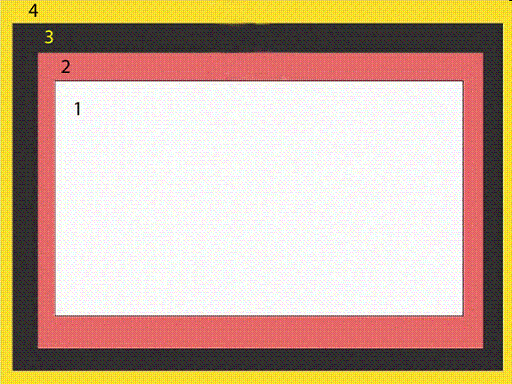 In the accompanying figure, the item marked 4 represents the ____.
In the accompanying figure, the item marked 4 represents the ____.
A. margin B. border C. content D. padding
?According to the FBI, organized crime organizations in many countries are increasingly turning to computer crime to target millions of potential victims.
Answer the following statement true (T) or false (F)
Using below table answer the questions that follows:
 a. What is the TCP source port number? b. How would you classify the source port? c. What is the TCP destination port number? d. How would you classify the destination port? e. Which flag (or flags) is set? f. What is the relative sequence number set to?