__________ is simply how often you expect a specific type of attack to occur.
A. ARO
B. CBA
C. ALE
D. SLE
Answer: A
Computer Science & Information Technology
You might also like to view...
The maximum speed at which data can be transmitted between two nodes on a network is called the ________
A) transmission rate B) throughput C) bandwidth D) node rate
Computer Science & Information Technology
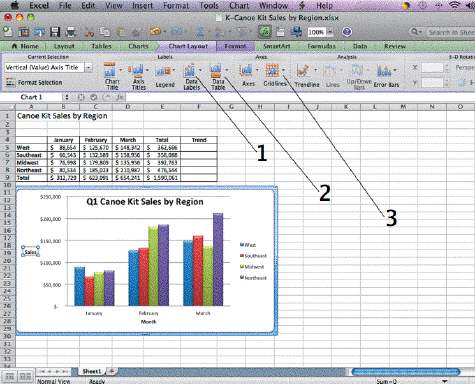 In the accompanying figure, Item 3 points to the Gridlines button, which you can use to enhance the visual appeal of the chart's ____.
In the accompanying figure, Item 3 points to the Gridlines button, which you can use to enhance the visual appeal of the chart's ____.
A. worksheet data B. axes C. data table D. plot area
Computer Science & Information Technology
A(n) ____ site, such as News360 and Flipboard, gathers, organizes, and then distributes web content.
A. content aggregator B. spider C. file-sharing D. indexing
Computer Science & Information Technology
Which of the following does PDF stand for?
A. Passive data file B. Portable document format C. Plain document folder D. Presentation document format
Computer Science & Information Technology