The essential difference between the Paintbrush tool and the Blob Brush tool is that the Paintbrush tool creates a stroked path and the Blob Brush tool creates a closed filled object.
Answer the following statement true (T) or false (F)
True
You might also like to view...
If an assigned task is ____________________, then the task belongs to that person to complete.
Fill in the blank(s) with the appropriate word(s).
Enhance the Inventory application that you developed in Tutorial 4 to prevent the user from entering input that is not a number. Use keyboard events to allow the user to press the number keys (0 to 9), the left and right arrow keys, the Backspace key and the Enter key. If any other key is pressed, display a JOption- Pane instructing the user to enter a number (Fig. 22.32).
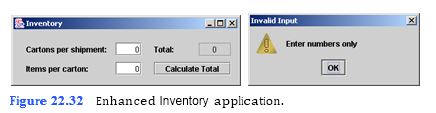
a) Copying the template to your working directory. Copy the C:Examples Tutorial22ExercisesInventoryEnhanced directory to your C:SimplyJava directory.
b) Opening the template file. Open the Inventory.java file in your text editor.
c) Adding a switch statement. In line 132 (in the cartonsJTextFieldKeyPressed method), begin a switch statement that determines whether a number key, a left or right arrow key or the Backspace key was pressed. Use KeyEvent constants VK_0, VK_1, VK_2, VK_3, VK_4, VK_5, VK_6, VK_7, VK_8, VK_9, VK_LEFT, VK_RIGHT, VK_BACK_SPACE and VK_ENTER. If one of these keys was pressed, use the break state- ment to continue execution.
d) Adding the default statement. At the end of the switch statement, add a default case to determine whether a key other than a valid one for this application was pressed. If an invalid key was pressed, display a JOptionPane that instructs the user to enter a number. Also, reset the text of cartonsJTextField to "0".
Describe the contents of the Privacy tab in the Internet Options applet.
What will be an ideal response?
_____ is a protocol for securely accessing a remote computer.
A. Transport Layer Security (TLS) B. Secure Shell (SSH) C. Secure Sockets Layer (SSL) D. Secure Hypertext Transport Protocol (SHTTP)