What user group is allowed to perform driver rollback?
A) All users
B) Administrators
C) Rollback supervisors
D) Microsoft rollback user
B
You might also like to view...
What are some of the tools used to exploit Web vulnerability?
What will be an ideal response?
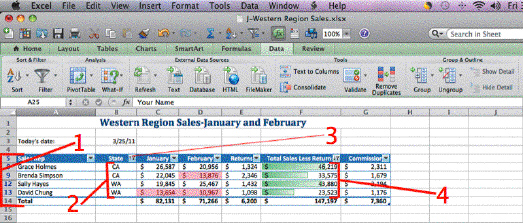 In the accompanying figure, Item 2 points to a column that shows that only the ____ for CA and WA have been marked in a filtered list of states.
In the accompanying figure, Item 2 points to a column that shows that only the ____ for CA and WA have been marked in a filtered list of states.
A. pop-up arrows B. check boxes C. data tabs D. dialog boxes
An administrator is building a development environment and requests that three virtual servers are cloned and placed in a new virtual network isolated from the production network. Which of the following describes the environment the administer is building?
A. Cloud B. Trusted C. Sandbox D. Snapshot
Describe the application development backlog that occurred during the 1980s.
What will be an ideal response?