_________ are used mostly in applications where timeliness of information is critical and where data are rarely processed exhaustively.
A) ?Indexed files ?
B) ?Indexed sequential files
C) ?Sequential files
D) ?Hashed files
A) ?Indexed files ?
You might also like to view...
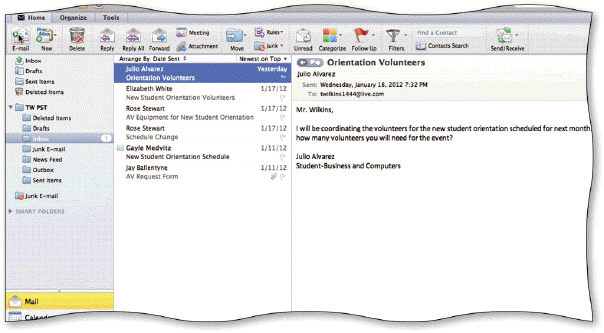 As shown the accompanying figure, Outlook directs newly received messages to the Inbox and displays them in the message pane.
As shown the accompanying figure, Outlook directs newly received messages to the Inbox and displays them in the message pane.
Answer the following statement true (T) or false (F)
Least privilege is a concept that denies all traffic to a resource unless the user is specifically granted access to that resource
Indicate whether the statement is true or false
A company is terminating an employee for misbehavior. Which of the following steps is MOST important in the process of disengagement from this employee?
A. Obtain a list of passwords used by the employee. B. Generate a report on outstanding projects the employee handled. C. Have the employee surrender company identification. D. Have the employee sign an NDA before departing.
We can use binary search to locate data in a linked list.
Answer the following statement true (T) or false (F)