When disaster threatens the viability of the organization at the primary site, disaster recovery undergoes a transition into ____.
A. business continuity
B. incident response
C. attack planning
D. crisis management
Answer: A
You might also like to view...
In a JavaFX FXML app, you define the app’s event handlers in a________ class, which defines instance variables for interacting with controls programmatically, as well as event-handling methods.
a. view b. model c. controller d. data
What is the most likely weak link when using asymmetric encryption for verifying message integrity and nonrepudiation?
A. the use of the sender's private key B. the hashing algorithm used to generate a message digest C. the source of the public keys D. the integrity of the private keys
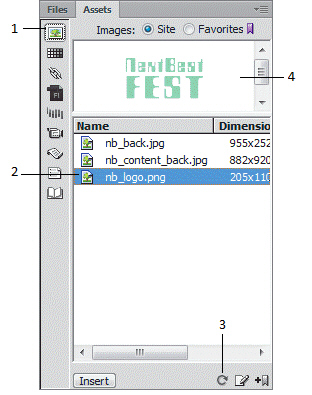 Click the item marked ____ in the accompanying figure to refresh the assets list.
Click the item marked ____ in the accompanying figure to refresh the assets list.
A. 1 B. 4 C. 3 D. none of the above
When customizing a JLabel, you can specify the __________ of that JLabel.
a) alignment of the text b) text c) size d) All of the above.