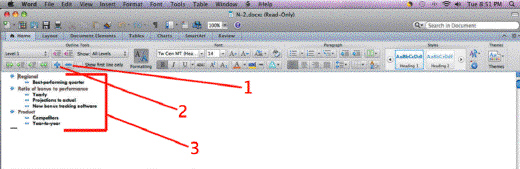
 In the accompanying figure, Item 1 points to the ____ button.
In the accompanying figure, Item 1 points to the ____ button.
A. Demote
B. Collapse
C. Promote
D. Expand
Answer: B
You might also like to view...
Which of the following refers to a computer used in a DDoS attack?
A) Botnet B) Victim C) Bot D) Handler
Match the following terms to their meanings:
I. Lookup field II. Combo box III. List box IV. Text box V. Multivalued field A. shows content that has been entered by a user B. shows selected values when closed and list of values when open C. shows a value that allows the user several data entry choices D. shows a list of choices E. shows a list from a table, query, or list of entered values
Overallocating resources may lead to project failure because the work will likely not get done in the time it was scheduled
Indicate whether the statement is true or false
What is rule number one for secure code?
A. threat analysis B. input cleansing C. misuse case D. data mapping