How does the CVE standard make network security devices and tools more effective?
A. the layered approach makes attacks nearly impossible
B. they can share information about attack signatures
C. it requires you to use compatible devices from one vendor
D. it warns an attacker that your site is being monitored
Answer: B
You might also like to view...
Answer the following statements true (T) or false (F)
1) A class template can be derived from a non-template class. 2) A class template cannot be derived from a class template. 3) A non-template class can be derived from a class template instantiation. 4) Templates can make available to the programmer the generality of algorithms that implementation with specific types conceals. 5) With regard to programming usage, consistency in coding is more important than optimality.
The term ____________________ is used to describe an electronic device, operating under the control of instructions stored in its own memory, that can accept data, process the data according to specified rules, produce results, and store the results for future use.
Fill in the blank(s) with the appropriate word(s).
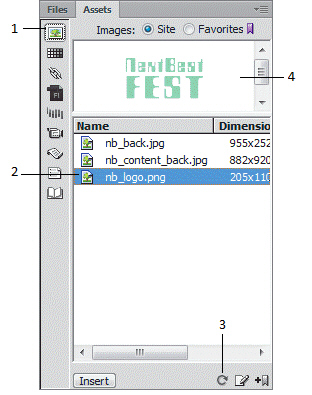 To open the panel in the accompanying figure, click the Assets tab in the ____ panel group,
To open the panel in the accompanying figure, click the Assets tab in the ____ panel group,
A. Files B. Images C. Resources D. Site
What is the definition of an elective surgery?
What will be an ideal response?