A user has called the help desk to report an enterprise mobile device was stolen. The technician receiving the call accesses the MDM administration portal to identify the device's last known geographic location. The technician determines the device is still communicating with the MDM. After taking note of the last known location, the administrator continues to follow the rest of the checklist. Which of the following identifies a possible next step for the administrator?
A. Remotely encrypt the device
B. Identify the mobile carrier's IP address
C. Reset the device password
D. Issue a remote wipe command
Answer: D. Issue a remote wipe command
You might also like to view...
All of the information about an individual or company that is displayed in a single row of a data source is a field
Indicate whether the statement is true or false
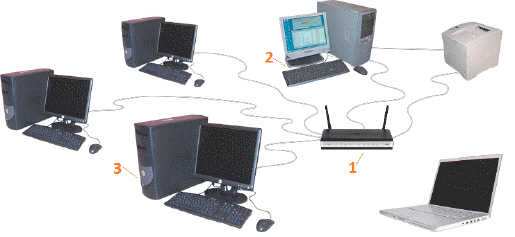 In the accompanying figure of a typical network configuration, Item 1 indicates a ____.
In the accompanying figure of a typical network configuration, Item 1 indicates a ____.
A. router B. server C. workstation D. printer
An absolute URL refers to the full Web address of a Web page or to a specific drive and directory.
Answer the following statement true (T) or false (F)
Critical Thinking Questions 11-1 ? Lisa and her team have finished the coding of a new application, and they are ready to begin testing. She asks Tina, a senior software tester, for help in designing the types of tests that Lisa and her team should perform. Lisa mentions that one program has been developed to interact with other programs, and she wants to begin by testing the programs individually. Tina tells her about a process in which a programmer simulates each program outcome or result and displays a message to indicate whether or not the program executed successfully. What is the name of this process?
A. Integration testing B. System testing C. Link testing D. Stub testing