Explain the rules that apply to using domain names.
What will be an ideal response?
Domain names always have at least two parts, with each part separated by a dot (period). For some Internet addresses, the far right part of the domain name is the country code, such as au for Australia, ca for Canada, dk for Denmark, fr for France, de (Deutschland) for Germany, and jp for Japan.. Many Internet addresses have a code denoting affiliation categories, such as com for business sites and edu for education sites. The far left part of the domain name identifies the host network or host provider, which might be the name of a university or a business.
You might also like to view...
When a subclass overloads a superclass method __________.
a. both methods may be called with a subclass object b. only the subclass method may be called with a subclass object c. only the superclass method may be called with a subclass object d. neither method may be called with a subclass object
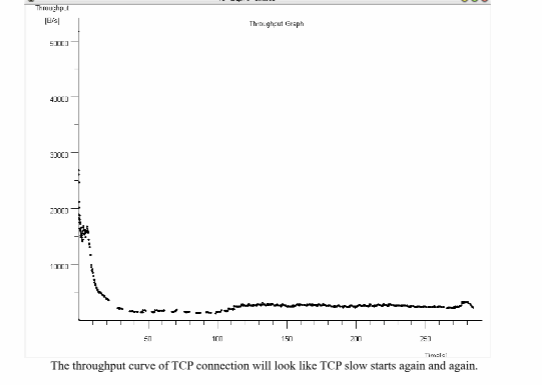
Generate a Throughput Graph to view the data rate of the TCP connection. How does the throughput change after the flood of pings is started?
Critical Thinking QuestionsCase J-2Jason is part of a class learning to use Dreamweaver to include dynamic content on web pages. One of Jason's classmates is confused about the differences between behaviors, actions, and events. When describing behaviors, what should Jason tell his classmate?
A. Behaviors are instructions. B. Behaviors are results. C. Behaviors are not seen by users. D. Behaviors are difficult to define.
In December of 2009, hackers broke into computer systems and stole secret defense plans of the United States and South Korea. The information stolen included a summary of plans for military operations by South Korean and U.S. troops in case of war with North Korea, though the attacks were traced back to a Chinese IP address. This is an example of a Trojan Horse.
a. true b. false