In Windows 10, you can create a picture password with ____________________.
Fill in the blank(s) with the appropriate word(s).
gestures
You might also like to view...
Logical security involves the information that is found on physical devices
Indicate whether the statement is true or false
Setting constraints on tasks will determine how Project 2013 will allocate resources
Indicate whether the statement is true or false
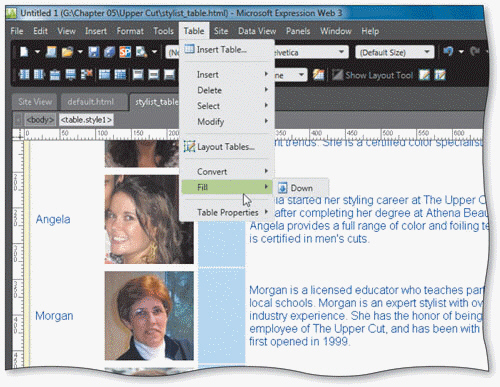 Using the accompanying figure as your guide, list the steps to fill a range of cells in the same column with existing content.
Using the accompanying figure as your guide, list the steps to fill a range of cells in the same column with existing content.
What will be an ideal response?
What is wrong with the following function?void _traverse (NODE* root, void (*process) (void* dataPtr)){ if (root) { process (root->dataPtr); _traverse (root->left, process); _traverse (root->right, process); } // if return;}
A. Traversal should be postorder. B. Traversal should be inorder. C. Data, left and right should be accessed as root.data, root.left and root.right. D. Root should be of type NODE, not NODE*.