This is a network's first line of defense against external threats.
A. port filtering
B. firewall
C. Network Address Translation (NAT)
D. MAC filtering
Answer: B
You might also like to view...
In Detailed view, you can print only in Menu Style.
Answer the following statement true (T) or false (F)
Firefox is a browser that is free of bugs, coding errors, or vulnerabilities.
Answer the following statement true (T) or false (F)
Given the following classes and their objects:
``` class C1 {}; class C2 extends C1 {}; class C3 extends C1 {}; C2 c2 = new C2(); C3 c3 = new C3(); ``` Analyze the following statement: ``` c2 = (C2)((C1)c3);``` a. c3 is cast into c2 successfully. b. You will get a runtime error because you cannot cast objects from sibling classes. c. You will get a runtime error because the Java runtime system cannot perform multiple casting in nested form. d. The statement is correct.
Configure the network according to the specifications listed. Make sure that you address both the internal and external access rules. Test your network carefully and then save your configuration. You will be asked to demonstrate your network to your instructor for grading. Make sure the ping command operates properly and the access rules are being implemented as specified in the requirements.
The objective of this project is for the students to gain experience configuring VLANs and access
lists for controlling data traffic into and out of the VLANs and the wide-area network connection.
This network setup has two separate sites, Site A and Site B, that are connected through Routers 1
and 2. The network address for Site A is 172.168.0.0. The network address for Site B is
192.168.35.0. IP addressing and subnetting within your network is up to you; however, plan your
network carefully.
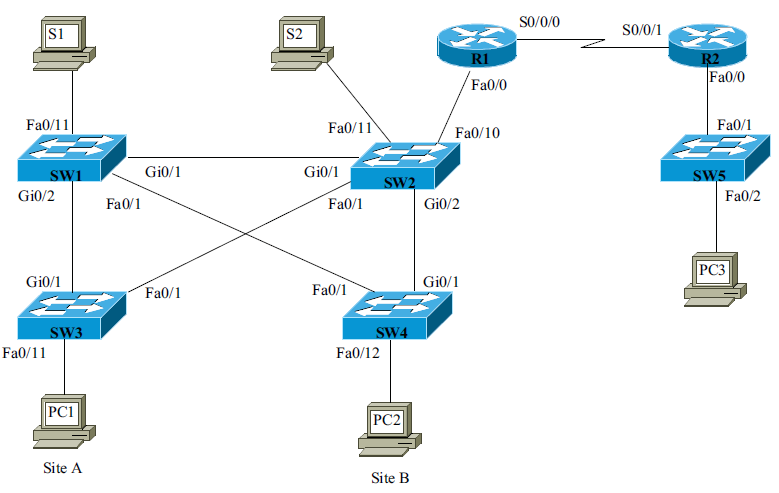
Specifics
Site A:
? Research VLAN (PC1), server (S1)
? Finance VLAN (PC2), server (S2)
Site B:
? Office LAN (PC3)
Internal access rules:
? Computers on the Office and Finance VLANs can communicate with the server (S2).
? Only the computers in the Research VLAN can talk to the Research server (S1).
External access rules:
? Only the computers in the Office and Finance LANs can access the wide-area network conne