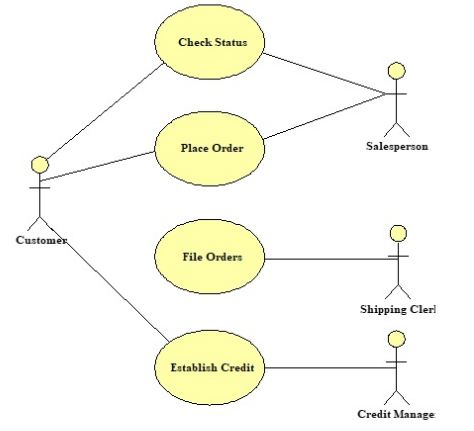
Draw a use case diagram for World’s Trend Catalog Division.
What will be an ideal response?
You might also like to view...
Which of the following is not a method provided by an array?
a) Sort b) Copy c) BinarySearch d) Reverse e) None of the above
Where do you change the order of query fields to change the order of query results?
A) In the design grid of a query's Datasheet view B) In the Criteria row of the Query Design view C) In the Show row of the Query Design view D) In the Relationship window of the Design view
____ is a technique used to gain unauthorized access to computers, wherein the attacker assumes or simulates an address that indicate to the victim that the messages are coming from the address of a trusted host.
A. Sniffing B. Spoofing C. Spamming D. DDoS
Paying a credit card bill online and using an ATM are examples of _________________________ in action.
Fill in the blank(s) with the appropriate word(s).