The protection of the information that might be derived from observation of traffic flows is _________ .
A) connectionless confidentiality
B) connection confidentiality
C) traffic- flow confidentiality
D) selective- field confidentiality
C) traffic- flow confidentiality
You might also like to view...
A mini-program that is executed without your awareness when you visit a website is called a(n) ________
Fill in the blank(s) with correct word
Which is the base class and which one is the derived class for Plane and Cessna?
A. class Plane is the derived class. B. class Cessna is the base class. C. class Plane is the base class. D. class Plane is an inherited class.
Two or more tables that contain duplicate data are an example of:
A) one-to-many relationships. B) data redundancy. C) many-to-many relationships. D) data backup.
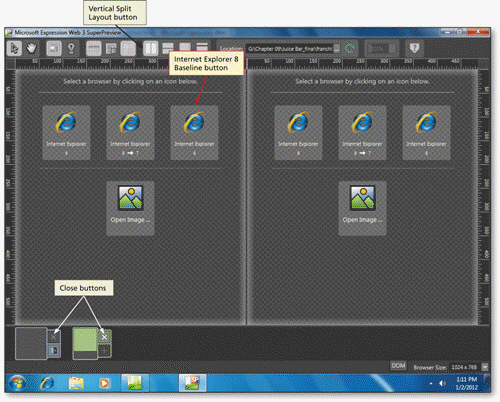 The SuperPreview feature in the accompanying figure allows you to compare the differences in Web pages in terms of ____ in different browser versions.
The SuperPreview feature in the accompanying figure allows you to compare the differences in Web pages in terms of ____ in different browser versions.
A. layout B. sizing C. positioning D. all of the above