Which Active Directory component is responsible for authenticating users when they log on to a workstation?
A. Trees
B. Forests
C. OUs
D. Domain controllers
Answer: D
You might also like to view...
Select the correct rules for encapsulation. If any rules need to be imposed in a particular order, then say so, mentioning which rules.
a) Make all class member variables public members of the class. b) Place the interface in the header file. What is the interface? c) Place the implementation in a separate code file (with file extension required by your compiler: .cpp, .cxx, etc), called the implementation file. What is the implementation? d) Having private members visible in the interface violates the philosophy of separating the interface from the implementation. Separate interface and implementation requires removal of all the private members from the class definition. You must put these in another part of the class definition in the implementation.
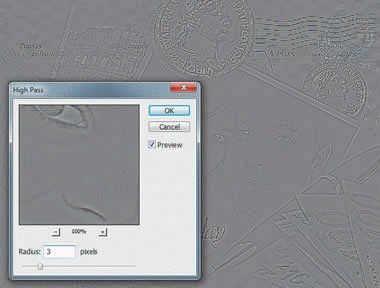 In the accompanying figure, why is most of the image filled with gray?
In the accompanying figure, why is most of the image filled with gray?
A. The filter removes everything but the midtones. B. Only the edge pixels are visible. C. The gray represents the edges of the image. D. None of the above.
If you need encrypted communication, you should use HTTPS port 443, which uses the ___________________________ protocol.
Fill in the blank(s) with the appropriate word(s).
TCP keep-alives are enabled by default on Windows XP, Windows Vista, Windows 7, Windows Server 2003, and Windows Server 2008, although any application may disable TCP keep-alives, if desired by its programmer.
Answer the following statement true (T) or false (F)