Which of the following should be configured to provide priority to voice traffic?
A. Port mirroring
B. DMZ
C. Qos
D. Trunking
Ans: C. Qos
You might also like to view...
Unauthorized users can access the network using a number of well-known techniques, such as_______—a method in which an attacker simulates the IP of an authorized user or host to get access to resources that would otherwise be off-limits.
a) IP stealing. b) IP simulating. c) IP spoofing. d) None of the above.
Providing adequate security on a corporate network involves all of the following issues except
a. authentication. b. restricting access to servers. c. proprietary software lockout. d. limiting physical access to networking equipment.
The area that holds all of the instructions the computer needs to start up is the RAM
Indicate whether the statement is true or false
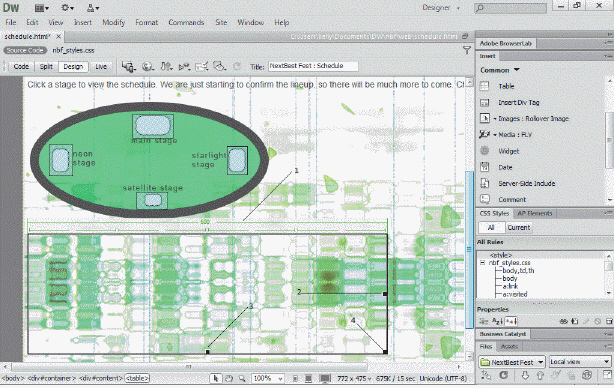 The item marked ____ in the accompanying figure is the table header menu.
The item marked ____ in the accompanying figure is the table header menu.
A. 1 B. 2 C. 3 D. 4