Which of the following protocols can be used to perform configuration management on a remote server using the MOST secure methods? (Select TWO).
A. SMTP
B. DHCP
C. RDP
D. SSH
E. TELNET
F. DNS
Answer:
C. RDP
D. SSH
You might also like to view...
Which of the following is the data type that can be used to create files and write information to them but cannot be used to read information from them?
a. ofstream b. ifstream c. afstream d. outstream e. None of these
No vCloud account is required in order to set up a vCloud virtual data center (VDC), although it is preferred.
Answer the following statement true (T) or false (F)
Arrays of three, four, five, six, or more dimensions can be viewed as mathematical n-tuples of order three, four, five, six, and so on, respectively.
Answer the following statement true (T) or false (F)
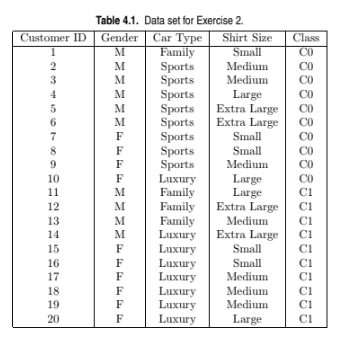
Compute the Gini index for the overall collection of training examples.
Consider the training examples shown in Table 4.1 for a binary classification
problem.