Hackers can spread worms over file-sharing networks and instant messaging links.
Answer the following statement true (T) or false (F)
True
Computer Science & Information Technology
You might also like to view...
On switch SW4, enable interface VLAN 1? What is the result?
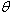
What will be an ideal response?
Computer Science & Information Technology
Which of the following is a touch input device?
A) Joystick B) Stylus C) Microphone D) Webcam
Computer Science & Information Technology
Finds the radius and height of a 2 liter can that produces the minimum surface area using Newton's method to approximate a zero of dA/dr
What will be an ideal response?
Computer Science & Information Technology
List information that can be extracted from web server log transactions.
What will be an ideal response?
Computer Science & Information Technology