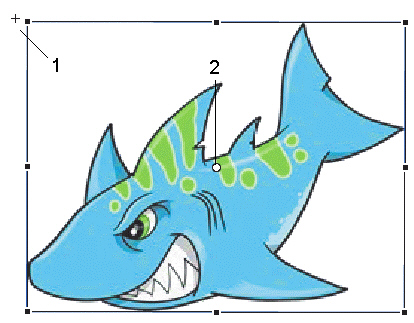
 The item marked 1 in the accompanying figure is the ____________________ point.
The item marked 1 in the accompanying figure is the ____________________ point.
Fill in the blank(s) with the appropriate word(s).
registration
You might also like to view...
Digital ____________________ security vulnerabilities are mostly associated with the IT infrastructure required to support interoperability.
Fill in the blank(s) with the appropriate word(s).
Predefined headers and footers insert placeholders with instructions for printing
Indicate whether the statement is true or false
Which of the following mitigation techniques can help prevent a high-jacked IM user account resulting from a password-stealing Trojan?
A. Disable the ability to send files through the system. B. Teach users never to share their account password. C. Teach users never to share their account name. D. Ensure that anti-malware software is installed and up to date on the user's computer.
To access the App updates screen, click or tap the ____ link in the upper-right corner of the Windows Store screen.
A. New apps B. Apps C. From developer D. Updates