The md5sum and sha1sum commands generate a checksum used to verify ____________________.
Fill in the blank(s) with the appropriate word(s).
file integrity
You might also like to view...
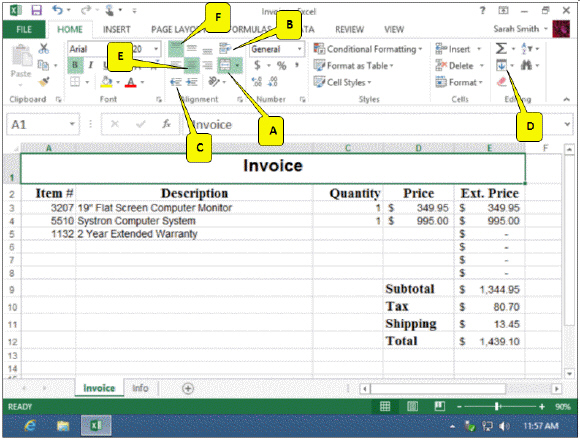 In the accompanying figure, which callout points to the button used to center cell contents?
In the accompanying figure, which callout points to the button used to center cell contents?
A. A B. B C. F D. E
In a structured reference what do you use to indicate a column heading or field name?
A) Brackets [] B) Quotes "" C) Parenthesis () D) Curly brackets {}
Discuss how Fitbit and Apple's Health App is an example of using IoT.
What will be an ideal response?
NIST recommends the documentation of performance measurements in a standardized format to ensure ____________.
A. the suitability of performance measure selection B. the effectiveness of performance measure corporate reporting C. the repeatability of measurement development, customization, collection, and reporting activities D. the acceptability of the performance measurement program by upper management