Each object you place on a form is called a(n):
A) index. B) control. C) icon. D) label.
B
Computer Science & Information Technology
You might also like to view...
For each of the four examples shown below, give the Gestalt principle it demonstrates.
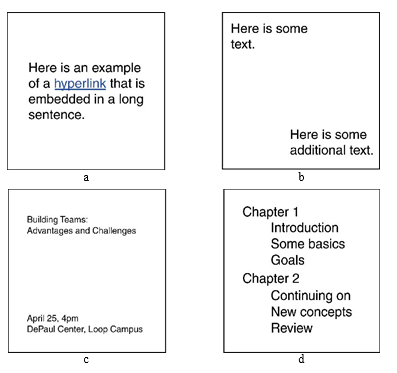
Computer Science & Information Technology
A kilobyte contains approximately one ________ bytes of data
A) hundred B) thousand C) million D) billion
Computer Science & Information Technology
__________ is the risk assessment deliverable that assigns a value to each TVA triple, incorporating likelihood, impact, and possibly a measure of uncertainty.
A. information asset value weighted table analysis B. risk ranking worksheet C. threat severity weighted table analysis D. TVA controls worksheet
Computer Science & Information Technology
What is the difference between passive and active IDSs?
What will be an ideal response?
Computer Science & Information Technology