Macro security can be edited in the ________
Fill in the blank(s) with correct word
Trust Center
Computer Science & Information Technology
You might also like to view...
Which of the following is the prototype for a member function have_birthday of a person class. The function increments a data member called age by 1.
a) int have_birthday (int ); b) void have_birthday ( ) const; c) void have_birthday (int ) const; d) void have_birthday ( );
Computer Science & Information Technology
Sorting library items by ____________________ puts items of the same type, like text, together in the library.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
A program that blocks unwanted or unsafe data is called a ________
A) proxy B) username C) LOPSA D) firewall
Computer Science & Information Technology
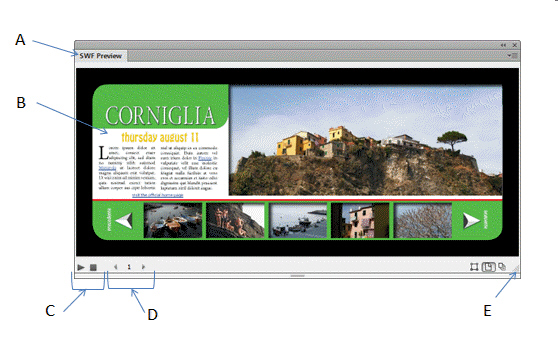 You click item E in the accompanying illustration to close the menu bar.
You click item E in the accompanying illustration to close the menu bar.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology