Any fact or set of facts, such as the words in a letter to a friend or the notes in a song, can become computer ____.
a. data
c. logic
b. information
d. hardware
Ans: a. data
Computer Science & Information Technology
You might also like to view...
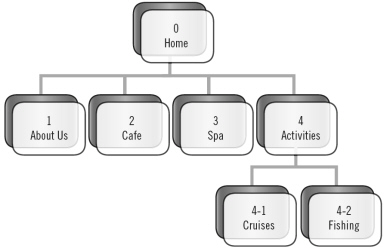 The accompanying figure shows a(n) ____.
The accompanying figure shows a(n) ____.
A. index B. data dictionary C. wireframe D. flowchart
Computer Science & Information Technology
When an attack occurs shortly after a security hole has been found and there is no patch available, this is called a(n) ________
Fill in the blank(s) with correct word
Computer Science & Information Technology
Both vSphere 6.0 and Hyper-V provide checkpoint merge capability which allows a snapshot to be applied to a running VM without the need to shut down and restart.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Which of the following allows an administrator to view malicious activity after it has taken place?
A. IDS B. IPS C. Port scanner D. Packet sniffer
Computer Science & Information Technology